ErkkiS_295148 Cirrus
Cirrus
Apr 03, 2018 Cirrus
Cirrusasm irule to unblock upon violation based on type
Hello,
I created a custom attack signature to block access to WSDL and sets Attack Type to "Information Leakage".
Works fine and blocks stuff.
blabla.com/ws/test?wsdl gets blocked.
Now I n...
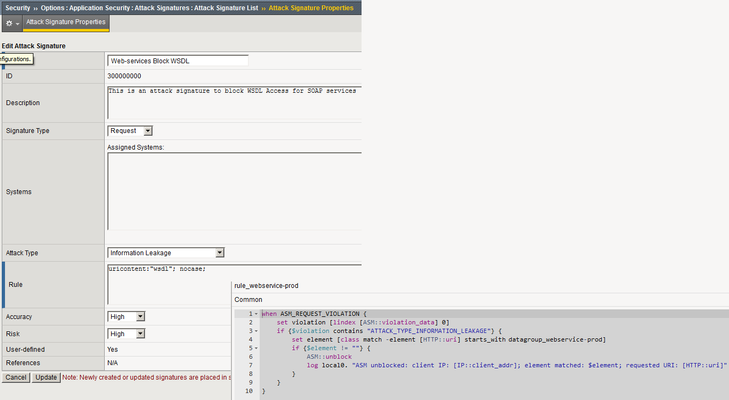
- Apr 04, 2018
Solved! YESSS!
First clue: https://devcentral.f5.com/Wiki/iRules.ASM__violation_data.ashx
Position Field Description **0 Violation** string that contains list of comma separated violations, see below the rquest side and response side violations for value options 1 support_id Unique id given for a transaction 2 web_application ASM Web application name 3 Severity it will be the most critical severity of all the transaction violations, possible values: Emergency, Alert, Critical, Error, Warning, Notice and Informational 4 source_ip Client IP. (in case trust xff option is enabled on the policy, this will be the xff ip **5 attack_type** string that contains list of comma separated attack types, see below for value options 6 request_status Can be “blocked” or “alarmed”Second clue: ATTACK_TYPE_INFORMATION_LEAKAGEInformation Leakage
So I am browsing the wrong hole which is 0 for matches instead of the correct one which is 5.
Third clue: Note: Starting version 11.5.0 this command is replaced by the commands ASM::violation, ASM::support_id, ASM::severity and ASM::client_ip which have more convenient syntax and enhanced options. It is kept for backward compatibility.
Also had to enable compatibility mode for Trigger iRule upon ASM event.